Aufs Corruption Issue 20 Docker/for-mac Github
- Aufs Corruption Issue 20 Docker/for-mac Github Pdf
- Aufs Corruption Issue 20 Docker/for-mac Github Download
- Aufs Corruption Issue 20 Docker/for-mac Github Free
Tour Start here for a quick overview of the site Help Center Detailed answers to any questions you might have Meta Discuss the workings and policies of this site. Here are the main improvements and issues per stable release, starting with the current release. There are confirmed reports of file corruption using the raw format which. Docker 1.12.1; Docker machine 0.8.1; Linux kernel 4.4.20; aufs 20160905.
Are you a Linux user who switched to Mac when you saw that Docker is now available as a native Mac app? Have you heard how great Docker is and want to give it a? Did you think that you could just take your Docker Compose file, launch your project, and have everything work out for you? Well you were right. Docker for Mac is a pretty smart invention.
It gives you the whole Docker API available from the terminal, even though Docker itself wasn’t created to work on Macs. To make all this possible, a light Alpine Linux image is fired up underneath with xhyve MacOS native virtualization. Because of this, you need to allocate CPU cores and RAM for the VM. Things won’t be as close to bare metal as they are in Linux. If you are – for example – a Java developer who uses Docker to run compiled JAR, you may even not notice the difference. At least, as long as you don’t try to do any heavy database work. Docker for Mac and Full Sync on Flush Issue First, let’s look at MacOS: “For applications that require tighter guarantees about the integrity of their data, Mac OS X provides the FFULLFSYNC fcntl.
The FFULLFSYNC fcntl asks the drive to flush all buffered data to permanent storage. Applications, such as databases, that require a strict ordering of writes should use FFULLFSYNC to ensure that their data is written in the order they expect.” In short, to keep our data safe, every change made in the database needs to be stored on disk in an exact order. This will guarantee that during power loss or any unexpected event your data will be safe. Actually, this makes sense — if you decide to setup a database inside Docker for Mac on a production environment In most cases, though, you’ll be using your machine for dev purposes where you don’t care to recreate the database from fixtures. If you have a Macbook, even power loss isn’t a threat.
In this case, you may decide to disable this. While reading about Docker issues on GitHub, I found a solution provided. Things will get a lot faster when you type those few lines into your terminal: $ cd /Library/Containers/com.docker.docker/Data/database/ $ git reset -hard HEAD is now at cafabd0 Docker started $ cat com.docker.driver.amd64-linux/disk/full-sync-on-flush true $ echo false com.docker.driver.amd64-linux/disk/full-sync-on-flush $ git add com.docker.driver.amd64-linux/disk/full-sync-on-flush $ git commit -s -m 'Disable flushing' master dc32fcc Disable flushing 1 file changed, 1 insertion(+), 1 deletion(-) Actually, someone even placed to make things easier. Does It Really Work?
I created a to check this. This test uses a standard Docker MySQL image without tweaks, and an image with sysbench installed. In my test case, I decided to use one thread (I only allocated one core for Docker on my Macbook) and a table with 10,000 rows. I ran it twice: once with flushing enabled (default), and once with flushing disabled. If you’re skeptical about performance gain after changing just one value from true to false, then let the results below change your mind.
For years, I advocated for developing inside of VMs or containers. Even wrote a very handy shell tool for managing the process. But a few years ago, I stopped, and just switched to developing on my local machine.
Working in VMs or containers adds a ton of complexity, for very little benefit. Installing databases is trivial, with any of `brew`, `yum`, or `apt-get`.
Your `bin/setup` script can take care of automating that for onboarding new developers. The same script gets used in your Dockerfile. And your CI system is there to as-perfectly-as-possible replicate production, to run your comprehensive test suite (you do practice TDD, right?) and catch things like 'forgot to add a library dependency to the setup script' and 'app broke because of a library version difference'. Since switching to local-only development, plus containers and CI/CD, my life has gotten a lot nicer. You'll never get the same environment locally as you do in prod.
That's why you have staging (you do have staging, right?). It's better to make the environment as close as possible to prod without adding massive inconvenience but docker both adds inconvenience and forces you to use it in production (which entails a whole other set of headaches) if you want close environmental parity, and even then, since it's lightweight virtualization there are hundreds of things which can behave differently between dev and prod.
Aufs Corruption Issue 20 Docker/for-mac Github Pdf
IMHO you either want very close environmental parity (in which case full virtualization is the way to go) or you don't, in which case running locally is fine. It's likely impossible to make volumes shared from the host to the container fast for all use cases. It's also likely impossible to make them work as expected on Windows where the host volume is NTFS and the container is Linux. So don't use shared volumes for code. At Convox we offer a Docker development environment in the 'convox start' command. We manage syncing code into the container by watching the host file system and periodically doing a 'docker cp' to get source changes into the container. It works great and shows the power of the Docker API for taking control of your containers.
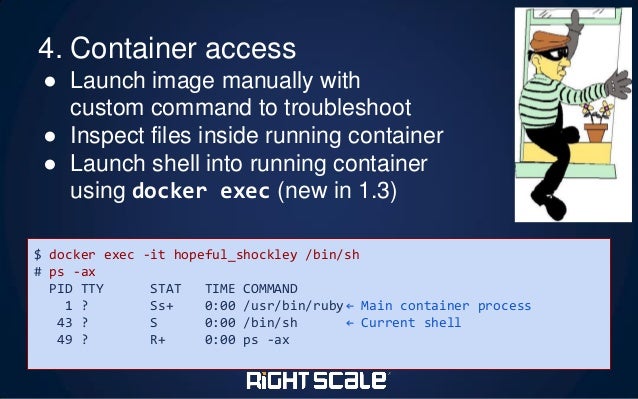
A bit more info is available here. Are you referring to this? Honestly, I see this as an antipattern, not because it generates extra layers, but because a Dockerfile isn't the right place to write a provisioning script.
When building apps, I keep a small number of shell scripts that live in a `bin` directory, that perform essential operational tasks. One script installs all the dependencies required to either run or develop the app; another runs all tests and exits with either success or failure; and the final script just runs the app. Docker then just runs those scripts, which are written deliberately to be easily read, and thus function as living documentation for the project. These same scripts get used, both by developers on a daily basis, as well as by our CI/CD system when prepping containers.
This also makes onboarding a snap: you run `bin/setup`, and your Mac or Linux box is good to go. And, because that script gets used every time the CI system spins up a build, it will never go out of sync with reality. The problem is that if you're building images a lot, Docker doesn't cache COPY calls because it doesn't know if the file has changed or not when calling the COPY command. So if you constantly build images and there are a lot of computationally intensive tasks within those scripts, but you've only changed one small item near the end of the script, your build time may be significantly longer by using the script than by putting it directly in the Dockerfile using the RUN command. I build a lot of modules within one of my Docker images for work, and while it doesn't change often, I would really not like to wait the 20 minutes if I really needed to push to production when I only change some certificate population segment at the end of the Dockerfile or something after a particularly intensive module build RUN step. It never gets out of sync, until somebody gets tripped up by some idiosyncracy of running the server directly on their machine instead of through Docker. One of the original benefits of containers is in its potential to reduce the disparity between dev and prod.
Aufs Corruption Issue 20 Docker/for-mac Github Download
If you're running containers based on the exact same image as dev and prod, then there are fewer reasons why something would only work on a dev machine. If your devs are using containers correctly, and building candidate images on their own machines, then there's no need for separate bin scripts. If your devs need separate bin scripts so that they can avoid installing and using Docker on their own workstations, then you're throwing out a lot of the benefit which containers give you. (I work on Docker for Mac.) Apologies for the inconvenience this has caused.
There was a race condition in a previous release which could allow multiple hypervisor instances to open the Docker.qcow2 simultaneously. Unfortunately this can corrupt the file by allocating the same physical block (cluster) twice, resulting in bad things happening. When this file-locking bug was fixed we also added an integrity check which checks the structure of the Docker.qcow2 on every application launch. For safety the app refuses to start if corruption is detected. I believe that in these cases, the corruption happened in the past and is now being detected since the upgrade. Unfortunately if the app refuses to start it makes it difficult to reach the 'Reset to Factory defaults' menu option.
The workaround described here is to remove the qcow2 and restart the app. Unfortunately containers and images will need to be rebuilt. For what it's worth after the integrity check and the locking fix went in, I've not seen any recurrence of this error. Please open an issue if you see any other problems! The 'Use compose-files to deploy swarm mode services' is really intriguing to me, especially when they quote this one liner: docker stack deploy -compose-file=docker-compose.yml mystack But there's no links to further documentation or anything.
Can this be used to deploy easily to a cluster of Droplets for instance? I feel like the low end/longtail deployment of Docker is really underserved. I want to use Docker for its devops merits, but I have yet to find a clear, concise guide for deploying a simple web app to one or a cluster of VPS instances for a modest traffic project.
Have you looked at Kubernetes? It's pretty dead simple to get a cluster up these days and the general abstractions they chose are really great. Service discovery, config and secret storage, control loops, autoscaling, even stateful containers these days.
100% worth giving it a shot, even just to say you've tried it. I've been using Docker for over three years now, and Kubernetes really is the realization of what I imagined containers would be like when I was just starting to use them in development.
It's pretty dead simple to get a cluster up these days The standard Kubernetes setup instructions are horrible. You need to run a bunch of shell scripts including cluster/kube-up.sh, which are documented to work on AWS, but which are completely untested before release, and which were recently broken for almost a month. I'm currently running Kubernetes under Rancher. It's still a pretty steep learning curve, with some very well-hidden but essential configuration parameters, but at least it actually works if you follow the instructions.
Your response is a massive mischaractarization of the status of kubernetes. Service discovery. When people say service discovery, they usually mean the ability for a given application to discover other copies of itself and other services & applications within a cluster. Kubernetes has this down. It has it down better than almost any other system. The 'Service' object in the API can be used for in-cluster service discovery, the service-account tokens can be used as a powerful means of introspection and discovery, etc. The things you link to are neither relevant.
The first is about making api-servers more HA and federation better I think (unrelated to user's services) and the second is a proposal which is implemented, done, and didn't really catch on tbh. It's implemented because, well, it didn't propose any code changes on top of all the features services provide now, just some standard metadata users can opt in to adding if they want that sorta thing. Secret storage The Secret api object works great. Adding vualt support is an ongoing feature, but it is in no way a bug, it's just a feature request/enhancement. It's good that kubernetes is evolving, but that doesn't mean that the feature isn't already working. Configuration scheme You linked the same issue as before, typo I assume. I have no clue what you're talking about though.
ConfigMaps are basically done. Downward API is nice. No clue what you think isn't 'fixed'. Please quit it with your FUD. You obviously have no clue wtf you're talking about.
Not only are you being very liberal with your use of profanity, you are not very accurate. I am not sure what is your personal peeve on this that you had to use words which have no place in a technical conversation. I linked to bugs and proposals that we are discussing on various sigs on slack.
Even aspects of load balancers and Service abstraction are insufficient and im part of some of the discussions. Secrets management being insufficient is the reason why there are suitable number of distributions with their own flavors of these. Your terming of Service Discovery proposal as a HA is laughable. HA in apiservers has been production ready for quite some time and well integrated in kops and kargo. Etcd recovery is still a hassle. You are mistaking documentation being marked as available with it being actually usable in lifecycle.
Are you aware that full tls in kubernetes is hard because some values are hardcoded? This causes etcd breakage in lifecycles. Kubernetes is not complete - im very bullish on its future, but I would recommend you stick to technical refutal more than personal ire. Since no one has actually provided links to more info about Compose V3, I'm happy to step in and help. But there's no links to further documentation or anything. Can this be used to deploy easily to a cluster of Droplets for instance?
This is exactly what the Compose V3 format (now native to Docker CLI, as noted in the article) is intended for. It creates/manages native Docker swarm services (and networks, etc.). The Docker official docs might take a minute to catch up in terms of Google indexing, etc., but you can always get the latest on GitHub to get a feel for what has changed from previous versions and/or how to learn Compose V3. Is a Markdown document outlining various Compose options. The main thing to keep in mind is that 'build' will not work as it has traditionally (use 'image' instead), and you gain additional access to a 'deploy' key to specify, e.g., number of 'replicas' (indentical copies for scale) of a given container. Is a V3 version of the canonical Compose Redis + Python 'page counter' app that may help to get the feel for things. In general: - 'docker deploy' will create or update a 'docker stack' (group of services) ('docker deploy' is shorthand/porcelain for 'docker stack deploy') - 'docker stack' will allow you to manage these stacks (list, remove, etc.), created from Compose files - 'docker service' will allow you to manage the individual services created (a service is a group of homogenous containers - think 3 copies of a webapp intended to sit behind a load balancer) Check out the '-help' text for each.
What do you mean? My Dockerfiles already use distro's package manager to install packages.
Do you you mean 'create a long-lived LXC container and use distro's package manager to install packages as needed?' The problem with that approach is you have no idea how to duplicate the server, nor how to roll back the changes reliably. For example: - Your distro upgraded a library, and the upgrade introduced a bug. For extra fun, this was not security upgrade so unattended-upgrade process did not install it, so only half of your servers have the bug. Your package list is incorrect.
Somehow, your old server ended up with an extra package (previous software version? Installed while trying to troubleshoot problems), and your new server does not have it. You have leftover files - either from the previous version of your software, or from the package you have had installed before.
Aufs Corruption Issue 20 Docker/for-mac Github Free
These are definitely fixable in LXC with enough effort - after all, Docker is not magic, and you can achieve a lot with LXC + shell scripts, and even more with LXC + shell scripts + chef. However, Docker is just so much easier and reliable than writing these scripts by hand.